Information Assurance Life Cycle
Nikolai Mansourov Djenana Campara in System Assurance 2011. To assist in accomplishing the goal of choosing and maintaining the best systems the information system process usually consists of six principal phases.
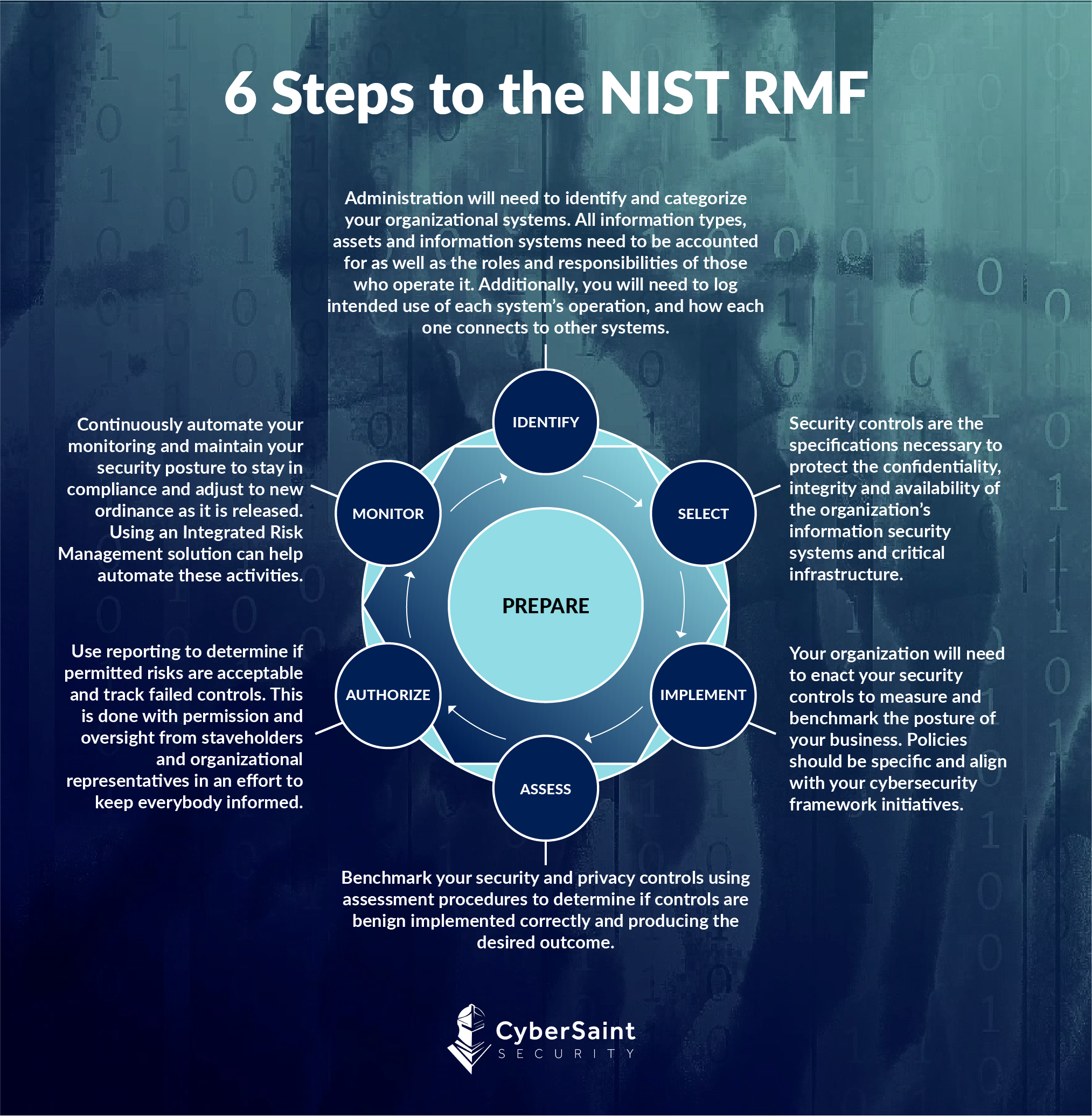
Infographic The Six Steps Of The Nist Risk Management Framework Rmf
At its core Information Assurance is about ensuring that authorized users have access to authorized information at the authorized time.

Information assurance life cycle. The software development life cycle SDLC does not work well where there is uncertainty to some extent. This free vulnerability scanner is capable of providing a. Information Assurance is a quick recipe for trouble.
SA-4 5 a Deliver the system component or service with Assignment. Information and vulnerabilities in web based applications. By its very name the info security lifecycle indicates that true information security is a process not a one and.
Security Responsibilities and Accountability Should Be Made. The system development life cycle is the overall process of developing implementing and retiring information systems through a multistep process from initiation analysis design implementation and maintenance to disposal. Information Assurance Risk Management Framework RMF Assessment and Authorization A.
SA-4 5 b Use the configurations as the default for any subsequent system component or service reinstallation or upgrade. Information assurance is often seen as a subset of information security that covers information governance cybersecurity and information assurance. CSRS-Corp Information Assurance Awareness Training and Education Program services are provided in a life-cycle approach that is we will guide your organization design develop implement and maintain an Information Assurance awareness training and education.
Life Cycle Engineering has been accepted into the National Security Agencys Commercial Solutions for Classified CSfC Trusted Integrator Program. Life Cycle Information Assurance Online Data Reveals Computer Security Threats With increasing intrusions of government computer networks information assurance IA has become a vital issue especially for the nations leading weapon developersThe USArmy Aviation and Missile Command AMCOM at Redstone ArsenalAlabama is the militarys. For 50 years and counting ISACA has been helping information systems governance control risk security auditassurance and business and cybersecurity professionals and enterprises succeed.
There are many different SDLC models and methodologies but each generally consists of a series of defined steps or phases. There are two uncertainties in life. Information Assurance and Security 1 Lab Information Assurance and Security PreMP1 MP2 PreLim Mid MP1 MP2 Midterm Question text.
4115 The implications to the common vocabulary and the integrated system model. Computer Network Defense CND. Acquisition Information Assurance IA Strategy Template from Defense Acquisition Guidebook 10 Program Category and Life-Cycle Status 20 Mission Assurance Category MAC and Confidentiality Level 30 System Description 40 Threat Assessment 50 Risk Assessment 60 Information Assurance Requirements 70 Acquisition Strategy 80 Certification and Accreditation 90 IA Testing 100 IA.
The basic system development life cycle is the process used to identify investigate design select and implement information systems. This is done through the inclusion of IA security re-quirements in the development of the information system or the application of those re-quirements later in its life cycle. Organization-defined security configurations implemented.
When communicating between different information sys-tems it is the responsibility of both parties to ensure the security of that communication. System life cycle considerations including the stages and the technical processes enabling systems and the supply chain has implications to the common vocabulary for describing system facts and the organization of the integrated system model. Although IT and cybersecurity and information assurance are complementary disciplines that virtually every company needs their different natures means they can be managed by different business areas.
The most visible advantage of the SDLC life cycle is that it provides control of the development process to some extent and ensures that the software system complies with all the estimated requirements. Information lifecycle management ILM is the effort to oversee data from creation through retirement in order to optimize its utility lower costs as well as minimize the legal and compliance risks that may be introduced through that data. Data integrity means maintaining and assuring the accuracy and consistency of data over its entire life-cycle.
An IA CA process represents. A Complete Guide to the Information Security Lifecycle. LIFE CYCLE ASSET MANAGEMENT Good Practice Guide GPG-FM-017 Quality Assurance March 1996 Department of Energy Office of Field Management Office of Project and Fixed Asset Management.
Death may or may not be the ultimate change depending upon your religious beliefs. State of Hawaii Business and ITIRM Transformation Plan Governance Information Assurance and Cyber Security Strategic Plan 7 In 2010 the Office of the Governor introduced a New Day. What is Information Lifecycle Management.
Our community of professionals is committed to lifetime learning career progression and sharing expertise for the benefit of individuals and organizations around the globe. When it comes to the safety of your data and technology systems its vital that your organization recognizes the reality of the information security lifecycle. BlackWidow can identify information that is not always so readily visible when viewing a web page such as e -mail addresses and links.
The major issue facing most of us in the information technology and information assurance fields is how to assure a reasonable level of.

Information Management Life Cycle Il Ciclo Di Vita Delle Informazioni Knowledge Management Life Cycles Knowledge

Mapping Document Management Processes Leveraging An Information Lifecycle Arma Magazine

Secure Sdlc Secure Software Development Life Cycle Snyk
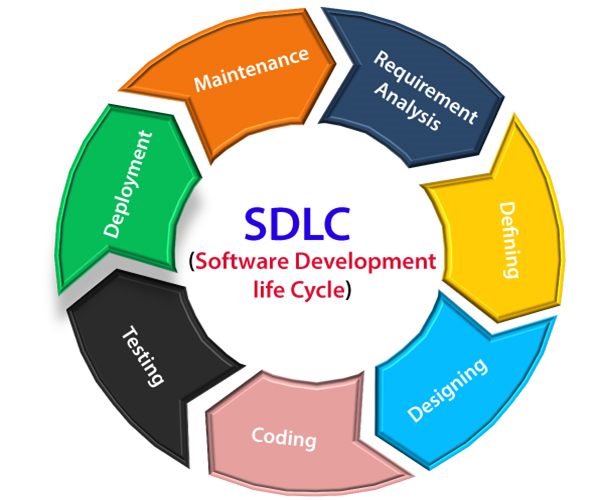
Systems Development Life Cycle The Systems Development Life Cycle By Sivakumar Raju Medium
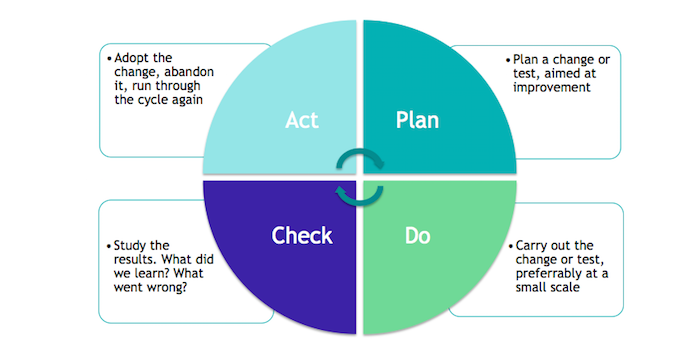
Ict Institute Information Security And Pdca Plan Do Check Act
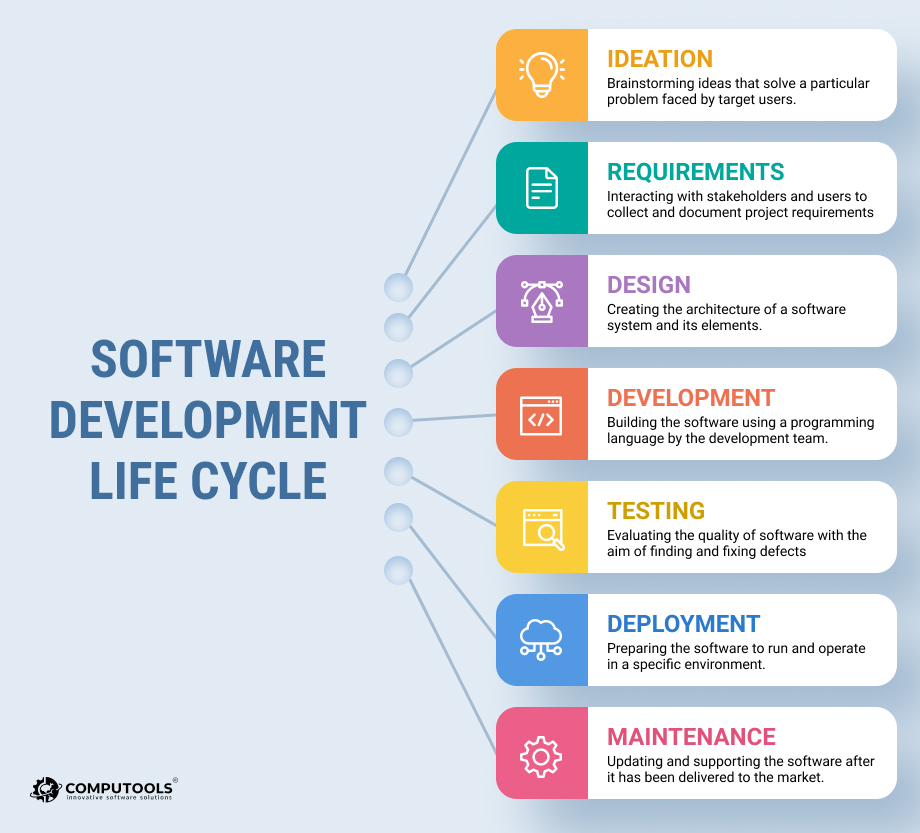
Software Development Life Cycle Sdlc Computools

Vulnerability Management Life Cycle Npcr Cdc
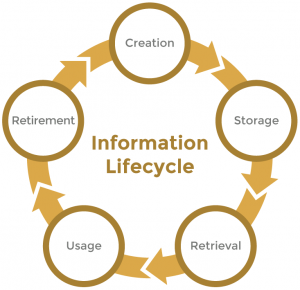
Phases Of Information Lifecycle Management Data Driven Digital Transformation Bbi Consultancy
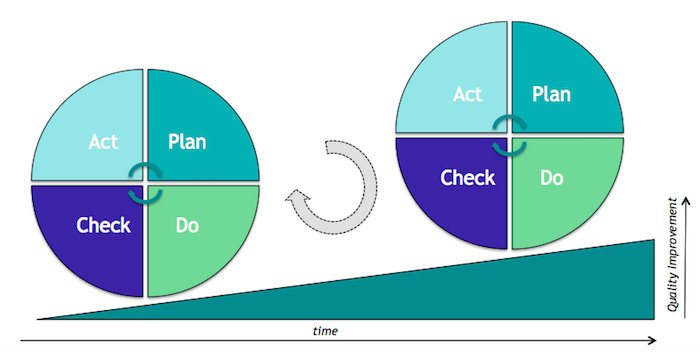
Ict Institute Information Security And Pdca Plan Do Check Act

System Life Cycle An Overview Sciencedirect Topics

Security Engineering 101 Wuson Private School

Dau News The Cybersecurity And Acquisition Life Cycle Integration Tool

Data Lifecycle Management Tracking Your Data Accurately Throughout The Information Lifecycle Hel In 2021 Life Cycle Management Data General Data Protection Regulation

How You Should Approach The Secure Development Lifecycle Dataversity

Data Life Cycle Management Information And Communications Technology Systems Engineering

Information Security Program Overview Securitystudio
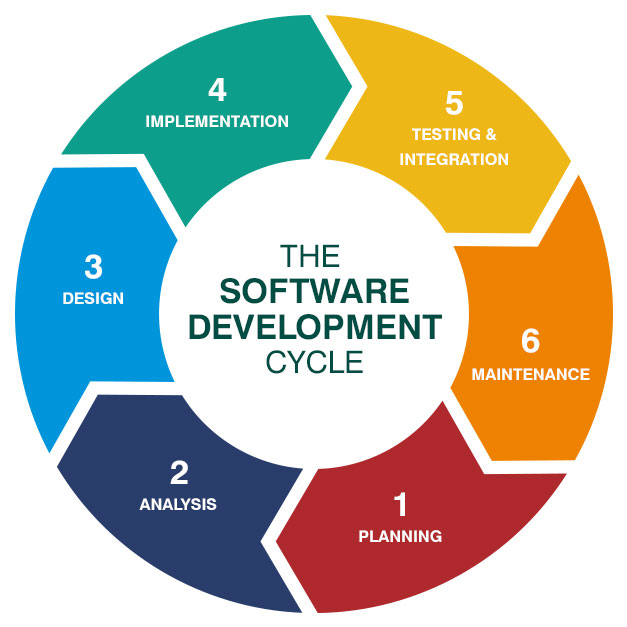
Software Development Life Cycle Sdlc Big Water Consulting

Quality Assurance Activities Should Follow Every Stage In The Software Life Cycle For Each Activ Agile Project Management Project Management Change Management

Secure Software Development Life Cycle Or Secure Sdlc Or Ssdlc Is A Systematic Approach And Software Development Life Cycle Software Security Security Training
Posting Komentar untuk "Information Assurance Life Cycle"