Unix Linux Operating System Security Audit Assurance Program
Managers need a framework to evaluate operating system security that includes an assessment of base security network security and protocols application security deployment and operations assurance trusted computing and open standards. When configuring Unix operating system security consider the critical principles of security known as the confidentiality integrity and availability CIA triad.
Auditing UNIX Systems A Case Study.

Unix linux operating system security audit assurance program. Obtain a listing of the various systems supported by the UNIX environment. Auditing LinuxUnix Server Operating Systems. UNIXLINUX Operating System Security AuditAssurance Program DownloadMember Only 2.
Auditing UNIX Linux -Ownership File Ownership and Access a really QUICK overview Only a superusercan change the ownership of a file. Buy Online keeping the vehicle safe transaction. Linux Operating System is widely used as server operating system around the world.
Even more in this case where they are so many different usage of UNIXLinux. August 2001 This report presents results of a detailed security audit of UNIX systems belonging to a fictitious company. UNIXLINUX Operating System Security AuditAssurance Program DownloadMember Only 2.
Audit Program for Auditing UNIXLinux Environments Questions Yes No NA COMMENTS Preliminary Steps. M Purchase the Book Provide feedback on this document Visit the Audit Tools and Techniques Knowledge Center community Visit the Unix- like Knowledge Center community. Some popular commercial and Open Source operating systems are Microsoft Windows different flavors of Unix BSD AIX HP -UX Solaris etc Mac OS and Linux.
Server auditing is an important task to ensure platform-level security in an IT infrastructure and to ensure the proper configuration of Linux server security. The project is open source software with the GPL license and available since 2007. The auditassurance programs reflect the IT Assurance Framework ITAF sections 3.
It performs an extensive health scan of your systems to support system hardening and compliance testing. Since this process is also addressed in the Identity Management AuditAssurance Program this review is limited to superuser access access to the operating systems configuration and security mechanisms and general user controls excluding users from access to. Both systems that we examined were running custom installations of Red Hat Linux 70 as the underlying operating system OS.
It does not attempt to cover all the technical aspects of the operating system and is much more a roadmap. Our community of professionals is committed to lifetime learning career progression and sharing expertise for the benefit of individuals and. The audit program covers security and administration of UNIX operating systems with particular focus on IBM AIX and SUN Solaris servers well as Red Hat LINUX OS.
Stacey Quandt Security is a perennial concern for IT administrators. This book does not address modifying the operating system kernel itself although many of the principles discussed here do apply. The auditassurance programs reflect the IT Assurance Framework ITAF sections 3.
In addition to incorporating security controls that. The main objective of this course is to give IS Auditors IT Controls and IT risk professionals a general overview of UNIX and LINUX operating systems its security and control issues and how to perform the audit of UNIX operating system to provide reasonable assurance to their organizatons management on the effectiveness and efficiency of controls required to guarantee adequate protection of. You will get Unix Linux Operating System Security Audit Assurance.
The following areas or aspects of the operating system and process controls will be reviewed and extensively discussed. If you are searching for read reviews Unix Linux Operating System Security Audit Assurance Program price. In earlier versions of UNIX Linux all users could change the ownership of a file that they owned this allowed one to give away a file to someone else.
Unix OS Security AuditAssurance Program. Like other operating systems it has its own pros and cons. If you searching to evaluate Unix Linux Operating System Security Audit Assurance Program price.
Lynis is a battle-tested security tool for systems running Linux macOS or Unix-based operating system. Policies procedures and guidelines for UNIX system administration. Chapter 5 - Unix and Linux Security.
Auditing system hardening compliance testing. Obtain a descriptionoverview of the UNIX system con guration. Obtain a map of the physical network to include.
In this study we compare Microsoft Windows and Linux security. For 50 years and counting ISACA has been helping information systems governance control risk security auditassurance and business and cybersecurity professionals and enterprises succeed. There are many objectives and goals to be considered when securing a operating system.
UNIXLINUX systems are subject to identity management the process of identifying and authenticating users and superusers. M Purchase the Book Provide feedback on this document Visit the Audit Tools and Techniques Knowledge Center community Visit the Unix- like Knowledge Center community. The Linux system has its own security configuration and management system to address the security requirements in an enterprise environment.
Le servers bridges routers gateways concentrators. Security Assurance Measure Requirements. Because of the crucial role of the operating system in the operation of any computer systems the security or lack of security of an operation system will.
Unfortunately this is a big security risk. This item is very nice product. This book describes a set of guidelines for writing secure programs on Linux and Unix systems.
June 11 2009 OpenBSD OS Security. Security is one of the aspects that are overlooked. It describes discovered vulnerabilities and proposes a.
We would recommend this store in your case.

Entry Level Qa Resume Lovely Quality Assurance Intern Resume Samples

Auditing Your Unix And Linux Infrastructure And Operating Systems It Audit Program Oxley Technologies Inc

Auditing Your Unix And Linux Infrastructure And Operating Systems It Audit Program Oxley Technologies Inc

Understanding Linux Audit Security Guide Suse Linux Enterprise Server 12 Sp3

Database Security Audit Program It Audit Program Oxley Technologies Inc

Unix Linux Operating System Security Audit Training Oxley Technologies Inc
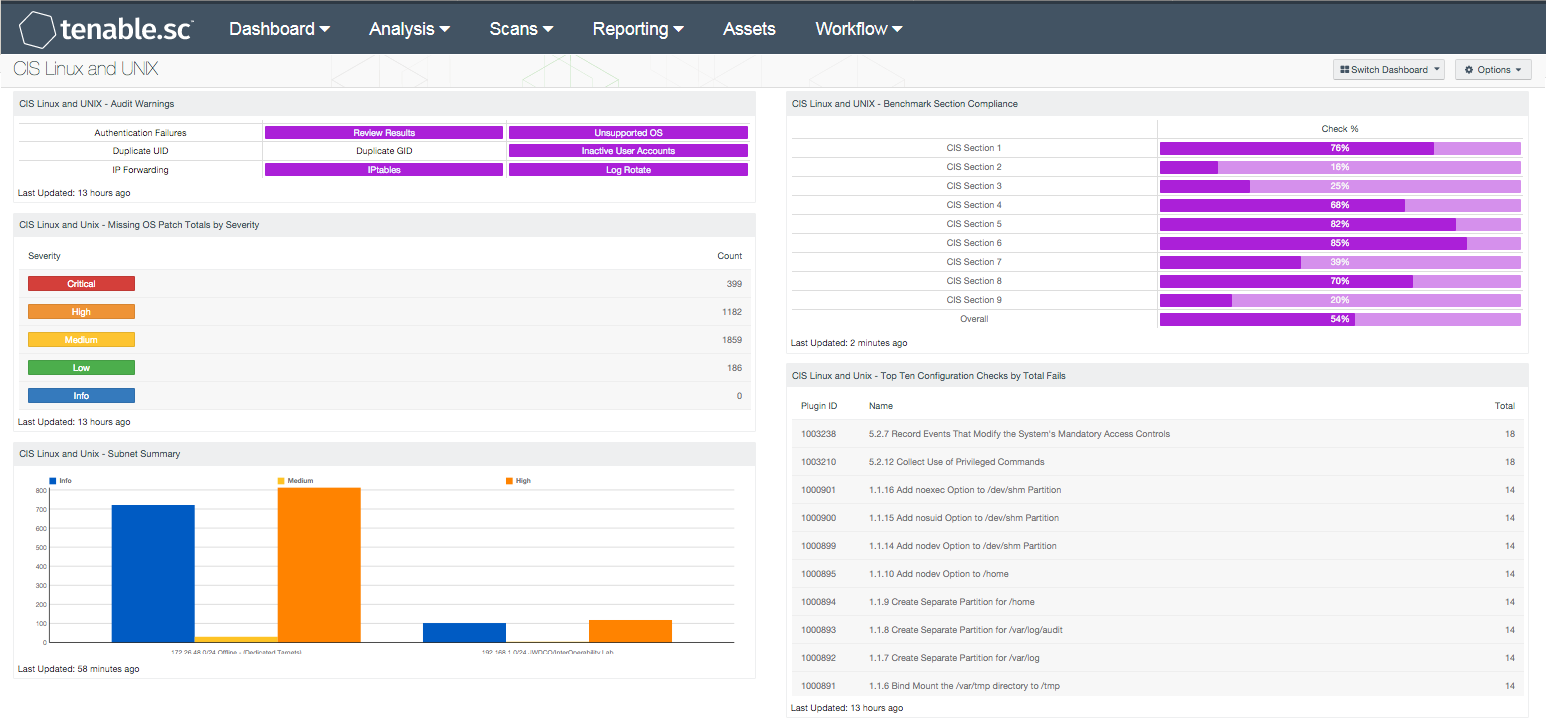
Cis Linux And Unix Dashboard Sc Dashboard Tenable

Auditing Your Unix And Linux Infrastructure And Operating Systems It Audit Program Oxley Technologies Inc

Secure Programming For Linux And Unix Howto The Linux
14 Best Network Security Auditing Tools What To Know In 2021

Auditing Your Unix And Linux Infrastructure And Operating Systems It Audit Program Oxley Technologies Inc

Cis Linux And Unix Benchmark Reports Sc Report Template Tenable
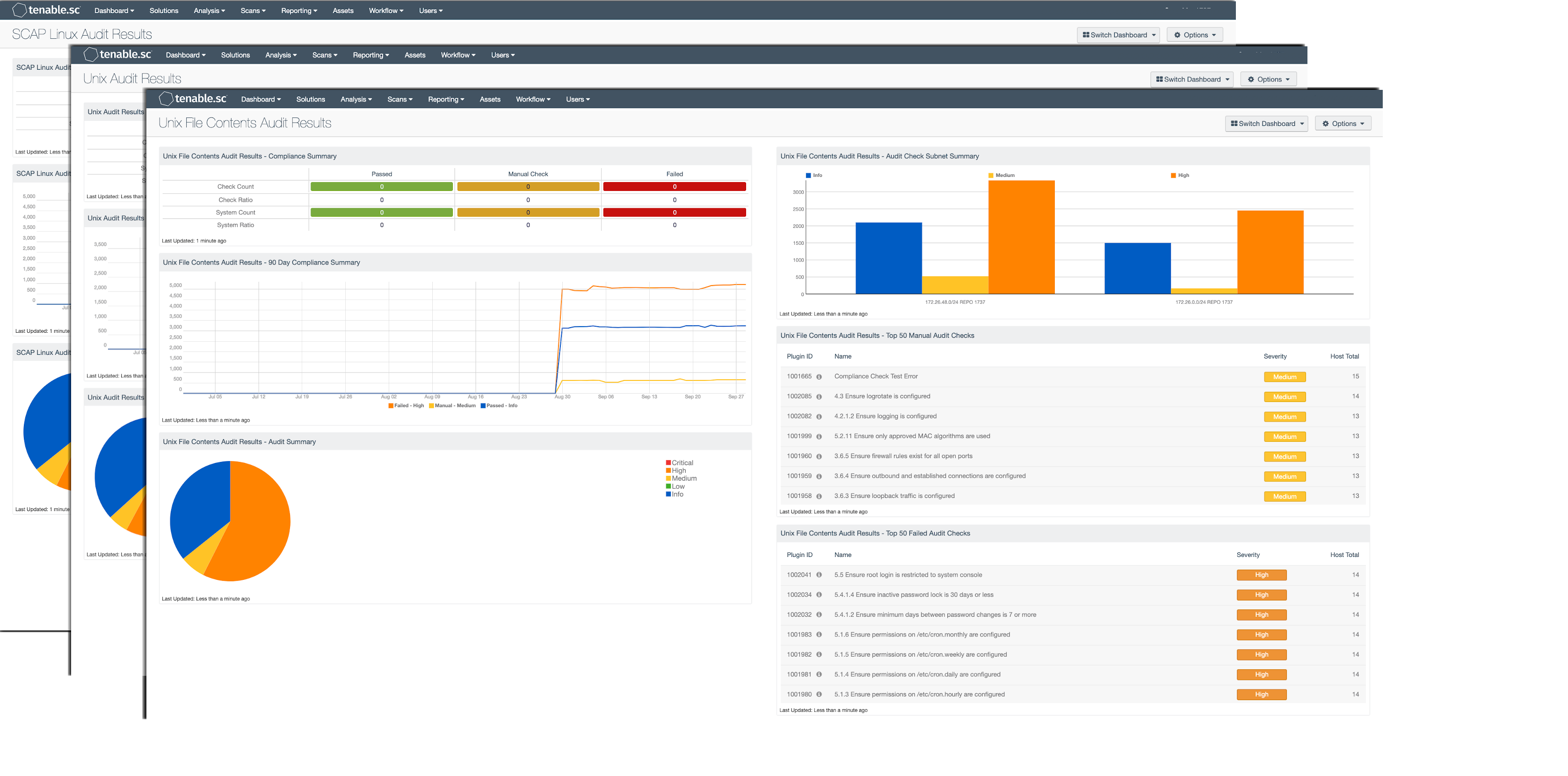
Linux Audit Check Dashboards Sc Dashboard Tenable

Ch 10 Operating System Security Control Punjab University Studocu

Pooled Audits On Cloud Service Providers

Is Standards Guidelines And Procedures For Auditing And Control Professionals

Unix Linux Operating System Security Audit Training Oxley Technologies Inc
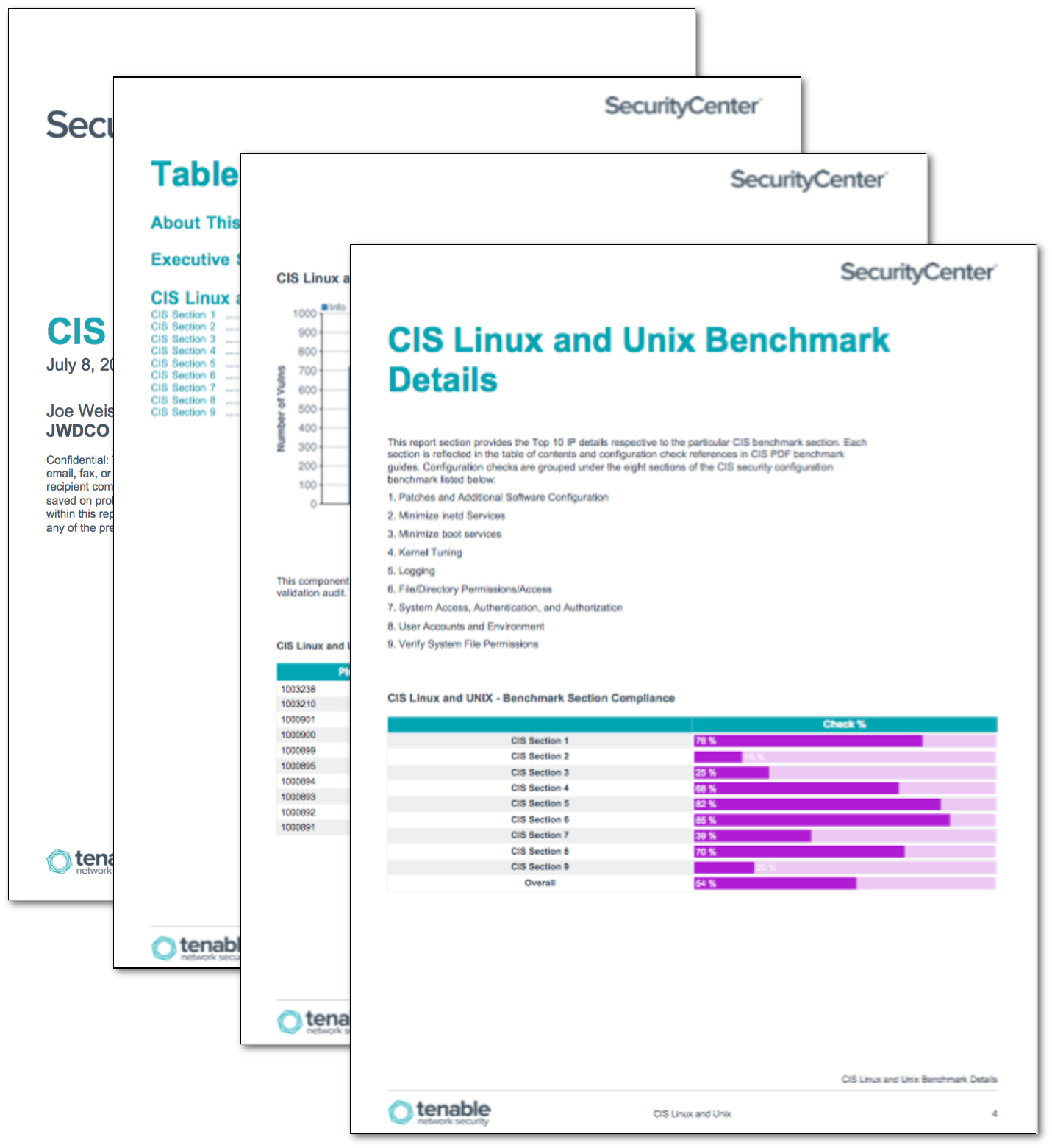
Cis Linux And Unix Summary Report Sc Report Template Tenable

Posting Komentar untuk "Unix Linux Operating System Security Audit Assurance Program"